What is tokenization?
Tokenization is a way for companies to protect sensitive data. Fundamentally, it allows companies to transform sensitive data into non-sensitive data. The nonsensitive data is called a ‘token’, hence the name.
The tokens are completely unrelated to the original data in terms of their values. However, there are still ways (such as the format) to link the tokens to the original data. This allows the company to continue business operations with a reduced risk of data leaks and breaches.
Here, we take a look at everything you need to know about payments tokenization. We discuss the benefits and drawbacks, the difference between tokenization and encryption, the types of tokens, and much more.
What is a token?
A token is a piece of data. The nature of this piece of data can vary wildly in terms of length and format. However, it will always replace other data. Using a small number of information retained from the original data, a token can effectively work as its replacement.
It is important to remember that a token has no value of its own. Without the original data, a token is basically meaningless. However, tokens are used in place of some of the most sensitive data worldwide, such as credit cards and identification numbers.
A great way to think about tokens is to imagine a hotel key card. When someone checks into a hotel, they usually get a keycard at reception once their identity has been authenticated and the reservation confirmed.
This keycard can then be used to access various areas in the hotel e.g. If you have special access to the VIP area or if you want to restrict children from the pool area but still allow them access to their rooms. This is much more convenient than having to carry identification papers or multiple keys at all times.
How does network tokenization work?
Network tokens are issued by the card scheme and stored by the merchant for transactions. Network tokens function by replacing the cardholder's credit or debit card data with a token that is unique to the customer, PAN, and merchant. Let’s break down the process into some simple steps:
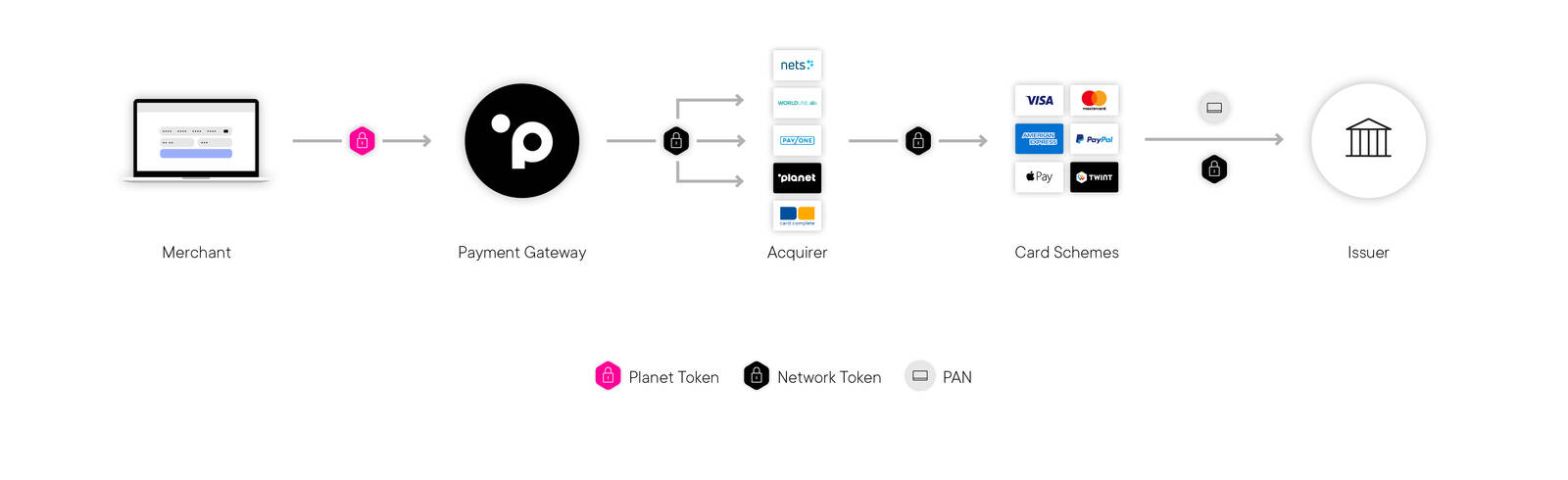
1. Token initialisation – The tokenization process is triggered when the customer makes an online purchase and enters their card details including their card’s PAN, CVV, and expiry date.
2. Token request – As soon as the merchant is in receipt of the customer’s card details, they share this information with their payment service provider (PSP). The PSP then requests a network token from the card scheme, such as Visa, Mastercard, Discover and American Express.
3. Token process – A network token is automatically generated by the card scheme, which it shares with the card issuer (the cardholder’s bank), and the merchant’s PSP.
4. Token storage – The merchant’s PSP shares the network token with the merchant. That token is typically stored by the merchant for future cardholder payments. Because it has been generated by the card scheme, the token is valid across the entire payment ecosystem.
5. Authorisation stage – The PSP sends the network token for that card from the merchant to the card scheme.
6. Token decryption – Once the card scheme receives the network token, it is decrypted, and the original card details are retrieved and shared with the card issuer so that they can be verified.
7. Payment processing of the token - The card issuer can now verify the card details, process the transaction, and approve the payment. Thanks to tokenization, the original card details were only ever shared between the card scheme and the issuing bank. The token was used at every other stage of the process.
What are the benefits of tokenization?
Let’s move away from analogies and into the real world. Here are some of the major benefits of tokenization:
- It is more difficult for hackers to gain access to sensitive data. This is because the data will be meaningless even in the case of a breach
- Tokenization does not usually require upgrading systems to match new standards. Encryption, on the other hand, might require legacy systems to upgrade.
- Tokenization does not require a lot of resources and is a cheaper alternative to other data security systems such as encryption.
- It makes compliance with regulators easier by adding an additional layer of security. We’ll go into more detail later on.
- It can provide new opportunities for efficiency in financial industries. Tokenization allows for services like one-click payment at merchants. This is because it allows companies to meet PCI DSS which is a requirement for one-click payments.
- Allows for alternative forms of contract settlement such as through the use of blockchain that may have benefits over legacy systems. An example of this would be settling a contract through Monero for privacy and anonymity.
What are the drawbacks of tokenization?
No system is perfect. This rings true for tokenization as well. Here are the major drawbacks of tokenizing:
- There are no clear regulations that deal with tokenization. This creates uncertainty that could be costly for companies later down the road. For example, a company may be forced to change its tokenization system if industrial regulations requires them to adhere to new standards.
- In certain cases, tokenized systems might have vulnerabilities that make it easier for them to be targeted and breached. For example, technical vulnerabilities may allow hackers to access sensitive data through the use of a token.
- Tokenization can be complex and may make the IT structure of a company a bit more difficult to understand. Any new IT technician would have to understand the entire tokenized system before they are able to maintain it or implement any changes.
- Tokenization requires the storage of sensitive data externally. The company choosing the vendor might be susceptible to data breaches.
- Not all payment processors support tokenization. This leaves companies and merchants with less options when it comes to picking payment processors compared to a traditional approach.
What is detokenization?
So far, we have talked about tokenization and its pros and cons. Once data has been tokenized, the issuer can then access the data through a process known as detokenization.
The original tokenization system is the only one that can access the sensitive data. The sensitive data is safely stored with the security vendor.
Many times, a token will simply be used once. An example of this is two-factor authentication. These tokens are then deleted afterwards as they have no further use. It is important to remember that tokens have no value on their own. They are simply a representation of the original data.
Types of tokens
There are many different ways through which tokens can be classified. A lot of research companies out there classify tokens in their own way. As such, there is no true way of classifying tokens. One of the reasons for this is that most of the industry is not regulated.
Here is one way one could classify tokens:
1. Payment tokens
Payment tokens are used to purchase and sell items digitally. The main advantage of using payment tokens is that there is no need for an intermediary. These tokens are used to purchase goods and services on an external network.
The industry of payment tokens is quite murky. They are not classified as securities. In fact, there is no regulation in most countries that classifies these tokens in any way. On top of that, they do not guarantee access to anything once they exchange hands. Great examples of payment tokens include most cryptocurrencies, such as Bitcoin and Ethereum.
Payment tokens are also sometimes known as currency tokens.
2. Utility tokens
Utility tokens are different from payment tokens. They represent something on the blockchain but are not used as a currency. Here, the token does provide its holder with a product or service. The issuer of the token decides this.
For example, a token may allow the holder to receive programming credits at the issuer. Or, the holder may be able to access certain services at a discount.
One thing to remember is that utility tokens can instantly lose their value. They are not considered an investment and are largely unregulated across the world. Examples include Golem and Brickblock.
3. Security tokens
As the name suggests, these tokens are akin to securities. These tokens are also sometimes known as asset tokens. Certain regulations around security tokens vary according to the country.
For the most part, security tokens promise a positive return. Many people consider them to behave similarly to bonds and other credit-based instruments. In many cases, security tokens are used to tokenize financial instruments such as bonds. Currencies and real-estate security tokens are also common.
Those based on real-world assets are usually known as asset-backed tokens, and others are known as equity tokens.
4. DeFi tokens
DeFi tokens are used, as the name suggests, for decentralised finance. These are used to power apps and services that can be used to transact on the apps.
For the most part, DeFi tokens are built on the Ethereum blockchain. These tokens can be used to engage in banking and investing. This can be done for both traditional assets that have been tokenized and for blockchain-related assets.
5. Non-fungible tokens
Non-fungible tokens are certificates that represent digital ownership of something. It could be something as simple as a screenshot of a meme or a painting by an artist.
NFTs became extremely popular for a short amount of time, skyrocketing in value before they came crashing down. While they are considered a fad by many, they still might be of some value when it comes to art.
Tokenization vs encryption
For those not too well-versed in the tech world, tokenization may seem like a concept that is quite similar to encryption. However, the two processes are fundamentally different.
Encryption is a method of changing the values of the data based on a precise cypher and encryption key. Users can then decipher the data as long as they have the key. Once something has been decrypted, it is back to its original state.
1. Problems with encryption
Because the data has been shuffled based on the cypher, the encryption key will reverse the exact same process. This can be a problem because anyone can access the data as long as they manage to access the encryption key. This can occur if a key holder is compromised. A hacker may also be able to access the key if it is written in a document.
Another problem with encryption is that many encryption systems can be brute-forced. This happens when a computer has enough time and power. It will try all the possible key combinations and eventually access the data. This is not practically possible for many advanced encryption systems. Many low-level systems can easily fall prey to brute-force attacks.
2. How tokenization differs
A token cannot be deciphered or reversed. In fact, there is no key or indicator that a person could use that will allow them to see the sensitive data behind the token.
Tokens can only be returned to their original form through access to additional data. This data is typically stored externally for safety reasons. As such, tokenization also tends to be a more cost-effective option.
This means that even if a data centre’s security is breached, the data obtained in a tokenized system will have no value for the hacker. The additional layer of security is precisely why tokenization has become more important in recent years.
There is no clear winner between tokenization and encryption. Whether to use tokenization or encryption depends on the company and the nature of its business. Many companies use them both. This is especially true for companies with a lot of highly-sensitive data.